How to Hide NGINX Server Version | Methods and Tools

Today’s web servers need to be open source, developed with cloud‑friendly tools, and be competent in adaptability and scalability.
A good way to achieve that is by developing microservice-based applications operating within containers. Multiple such use cases require Nginx.
What is Nginx?
Nginx is a popular open-source web server and is one of the most popular load balancer and caching tool.
It is used as a reverse proxy to forward client requests, a load balancer to distribute tasks, a mail proxy, and a tool for HTTP cache optimization and reduction of delay in browsing.
Also, it can be coupled with cloud architecture to maximize performance. Cloudflare is one such example where Nginx can be used. Hence a lot of ventures look forward to integrating Nginx into their workflow more and more.
With such diverse purposes, we might need to hide the Nginx server version, or any web server for that matter. Using a cloud tool can help enhance, Privacy, secure data encryption, and high download speeds are some of the key parameters to tackle, and withholding behind the scenes information from the layman is a decent way of going about it.
Image Source: morioh.com
So how do we do it?
Old Version of Nginx:
If you're using an old version of Nginx and want to hide it openly, you can avail of the Nginx server tokens directive in your Nginx configuration. This directive hides the version in your HTTP headers and default error pages. Snoop around for the nginx.conf file for the purpose.
To do this, just set the server_tokens to off. It is ‘on’ by default.
To Check the Current Nginx Server Header Information
The terminal command curl --head yourdomain.com can check your current server information.
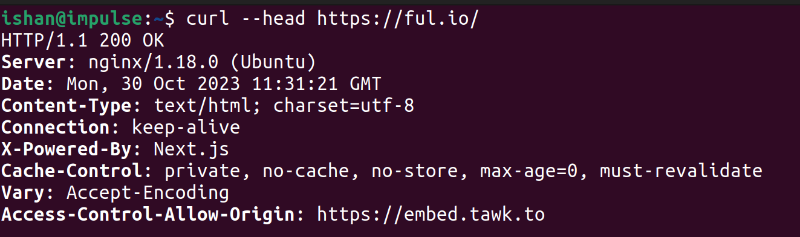
You can also use the HTTP / HTTPS Header Check tool by Webconfs, security headers, and Mozilla observatory, which is beyond the scope of this tutorial. The simplest method is to use the curl command. Execute it on the shell directly to find Nginx server version in Linux.
Hide Nginx Version:
- To access the Nginx hide version, go to the HTTP status code, and the default configuration would have the version number; hide it, and you are good to go.
- This step will harden web servers towards cyber-attacks that might infect them. This solution applies to the Nginx version on Linux or UNIX.
Editing the Nginx Configuration File:
- Open the configuration file using a text editor and go to the # HTTP Options and ## lines.
- Now add the new line server_tokens off. The Nginx server tokens directive shows the Nginx version number and its Operating system on error pages and in the header field of the “Server” HTTP response.
- You can check the server information and verify if it is working.
- Save the file to configure it successfully, and restart Nginx server so that the changes reflect.
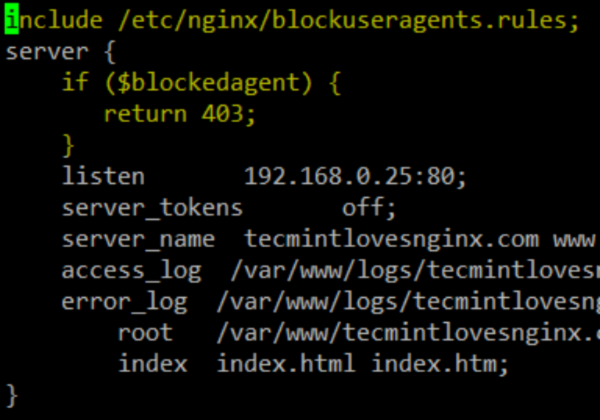
Image Source: www.tecmint.com
What To Remember While Hiding Nginx Version
The step mentioned above will only hide the server version number. It doesn’t hide the server signature or its name.
How To Hide the Server Name
- To hide the server signature or the name, it's possible to compile Nginx from source. Include the –build=name option to set an Nginx during the build to specify the signature or name.
- In the case of running the PHP scripting language in your Nginx web server, you have to hide the PHP version number.
To Hide PHP Version Number
To do this, we must first load the PHP configuration file. Therefore, creating a backup of your PHP configuration file is essential.
- Then, make changes to the PHP configuration file. If you can’t find the location of this configuration file on your server, run the command grep “Loaded configuration file” to find it.
- Then, locate the keyword expose_php and set its value to ‘off.’
- Save the changes and restart to see if the changes reflect in the web server.
Also Read: Know about CMC Framework PHP
Checking if the PHP Version Number Is Hidden
Use the following commands to check if the HTTP response header is still displaying the PHP version number.
-head –mime_header http://localhost
-head –mime_header http://server-address
Here, the –head sends the HEAD request for the mime headers, and the –mime_header displays the MIME header of the document along with its source.
How To Hide the Use of Nginx Altogether
As we hide the Server header, we might notice the default error pages by Nginx still display the “Nginx” word. This can be solved by using a couple of methods.
Using Nginx-MOD
Use Nginx-MOD and specify the server_tokens none; in the Nginx server tokens configuration.
Note that only Nginx-MOD supports this none value for the server_tokens directive.
Source Code Change
You can also obtain Nginx hide version by recompiling it from the sources and by adjusting Nginx sources. This step prevents Nginx software information disclosure. Then you can recompile Nginx.
(Note: This step is discouraged as doing this is obsolete, and it's a complicated solution for a simple change. It could result in a broken build as well.)
GetPageSpeed Servers
GetPageSpeed provisioned servers, and any similar servers performing monthly maintenance can hide the Server header for you.
Such servers make use of the Citrus Stack. That panel-less server stack is high-performance driven and already includes Nginx-MOD as the web server by default. Now you can alter the web server_tokens to ‘none’ as we discussed.
Hide the Server Header
Use third-party modules such as ngx_security_headers. To install the module, access the RPM repository available for Nginx.
Now change your nginx.conf to set hide_server_tokens on.
This step eliminates the Server header from the responses.
Block HTTP User Agents in Nginx
- You can also block HTTP User Agents in Nginx by placing a server block definition with rules.
- You can replace your server’s IP with 192.168.0.25 and choose a different string for the –user-agent switch of wget.
- This change can prevent web crawlers and bots from contacting system resources.
Limit the Number of IP Connections
- Use the limit_conn_zone parameter to limit the number of IP connections outside the server block and in an HTTP context.
- Use the limit_conn to limit the number of IP connections in an HTTP context, server block, or location context directives.
- You can set the maximum number of connections to limit the number of IP connections and even reduce the number to 1.
- This is a restrictive but convenient method to ward off cyber attackers and prevent potential breaches or exploits of known vulnerabilities.
Filter the Access Log for Information
Often servers are worked upon remotely via ssh access. In such cases, the access log contains useful information, you can inspect.
- You can also filter the access log for information on the Client IP, HTTP request type, Resource request, Server block which answers the request, and Browser type.
Avoid SSL and update to new versions/TLS
- Shun SSL in any of its versions. The security vulnerabilities made it completely replaceable by 2019. Instead, use TLS.
- Place the ssl_protocols TLSv1, TLSv1.1, TLSv1.2 in a server or HTTP context. To do this, use the file ssl.conf in your virtual host file or a separate file via the include directive.
Overall, the results show using Nginx-MOD is essential to install new directives and make source code changes. By using one or more methods discussed above, you won’t need to worry further about how to hide the Nginx version on your server.